The Problem
IT services require configuration. Part of the configuration are secrets that you don't want to see exposed. Common examples are database credentials or random values that protect session cookies or authentication credentials. If you are developing software, things tend to get worse with build pipelines, distribution certificates and access keys.
Compromised secrets can lead to user account takeover, data theft, build chain attacks and other costly problems. Bad reputation, the loss of intellectual property and potentially huge legal fees are just a fraction of the possible costs.
The solution
Psono offers with the latest version of psonoci protected environments. Protected environments allow you to run processes and configure them through environment variables without exposing them to the system. These environment variables are loaded securely from Psono, never stored anywhere on the server and are only exposed to a single process.
- Secrets do not end up in any backup
- Offline copies are useless for attackers without network access to Psono.
- Environment variables are isolated so other processes do not have access.
- Secrets can be shared across servers, so standbys or HA siblings don't run with different configurations.
- API keys can be easily revoked at a central place.
- Workflows can be established so administrators never gain access to the actual secrets.
- Third party services (like e.g. github or heroku) do not have your secrets in their database.
How does it work?
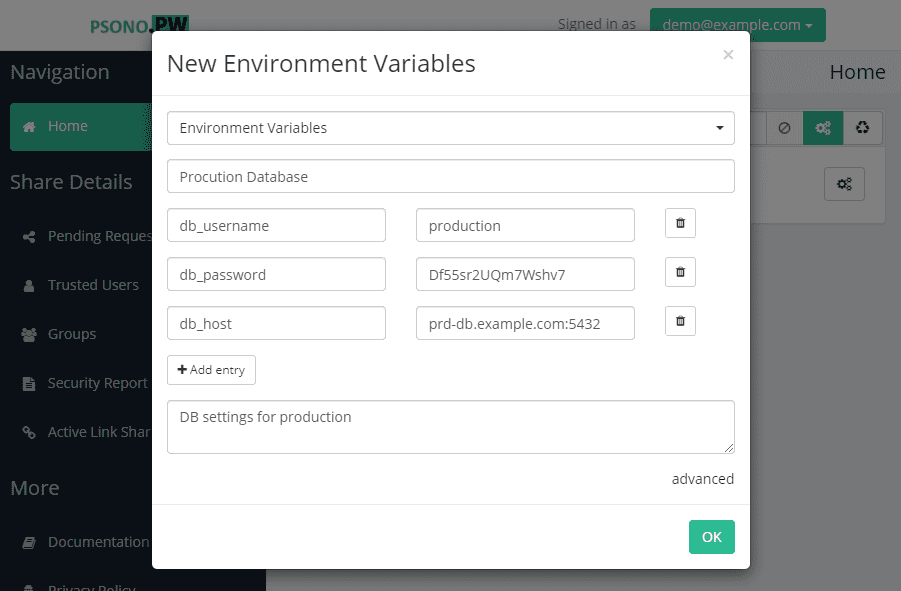
First you have to create an environment variables secret. Please take not that a single secret can hold multiple environment variables so you can group environment variables by e.g. an environment or just because they belong together like a database user and a database password.
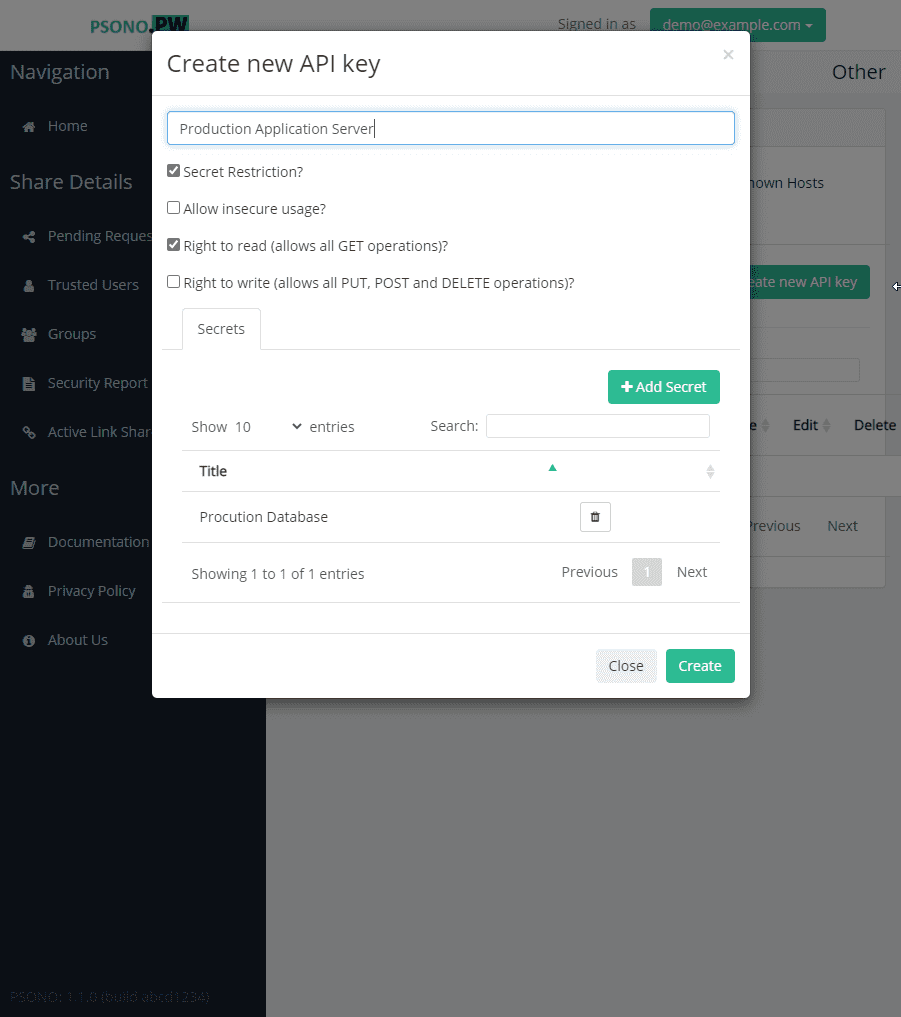
Afterwards you create an API key and allow this API key to access your new environment variables secret.
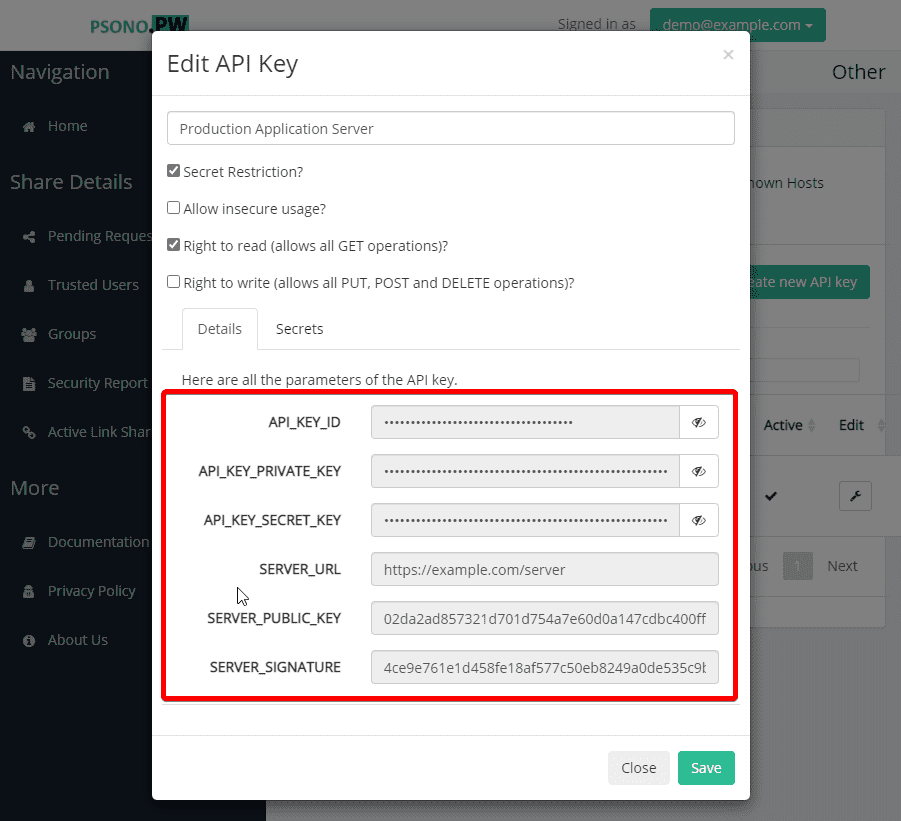
Now take note of the API key secrets, as these parameters are the only parameters that are directly exposed to the system.
Install psono ci on your server or in your build pipeline with a single command:
curl https://get.psono.com/psono/psono-ci/x86_64-linux/psonoci --output psonoci && chmod +x psonoci
And instead of just running ./some_command you spawn your process like this:
psonoci \
--api-key-id eaee77c6-169f-4873-9be3-f2613149baa9 \
--api-secret-key-hex c8321d7a8e5b1f5ec3d969ecb5054c7548a1c709ddab2edae2ff7ff028538917 \
--server-url https://example.com/server \
run -- ./some_command
For simplicity we pass the parameters like --api-key-id or --api-secret-key-hex as arguments yet you can also
configure a configuration file instead.
For demo purposes we created this small python script service.py which prints all environment variables and arguments that
were passed to the script.
#!/usr/bin/python3
import os
import sys
print("args: {}".format(sys.argv))
print("environment: {}".format(os.environ))
Instead of executing for example ./service.py --whatever=argument_1 we can execute it like this:
psonoci \
--api-key-id eaee77c6-169f-4873-9be3-f2613149baa9 \
--api-secret-key-hex c8321d7a8e5b1f5ec3d969ecb5054c7548a1c709ddab2edae2ff7ff028538917 \
--server-url https://example.com/server \
run -- ./service.py --whatever=argument_1
We get the following output:
args: ['service.py', '--whatever', 'argument_1']
environment: environ({'db_host': 'prd-db.example.com:5432', 'db_password': 'Df55sr2UQm7Wshv7', 'db_username': 'production'})
As we can see all arguments were passed along proper and all the environment variables that we previously configured were available to the process. There are flags in place that allow you to pass the normal system environment variables too and extend them with the ones from Psono. More detailed information can be found here in our documentation for psonoci.
I hope you liked our small excursion demonstrating how Psono can help to protect your infrastructure. All this would not be possible without Bernd, the mastermind behind this feature, so thank you so much Bernd!