Reusing passwords is extremely proplematic. It is sad, that people do not know about the involved risks for their account and data. Attackers use email addresses and passwords from previous breaches and try to gain access to other websites. Password managers that generate random passwords are a perfect measure against those attacks, generating random passwords for every website. But what about all those old passwords? We have just released a new feature, allowing users to check their passwords against a huge database with the help of haveibeenpwned.com. With this new tool in our belt its possible to check passwords against a dataset of nearly 5 billion accounts with passwords.
Thank you haveibeenpwned.com!
The Pwned Passwords service was created in August 2017 after NIST released guidance specifically recommending that user-provided passwords be checked against existing data breaches . The rationale for this advice and suggestions for how applications may leverage this data is described in detail in the blog post titled Introducing 306 Million Freely Downloadable Pwned Passwords. In February 2018, version 2 of the service was released with more than half a billion passwords, each now also with a count of how many times they'd been seen exposed.
(Source: https://haveibeenpwned.com/Passwords)
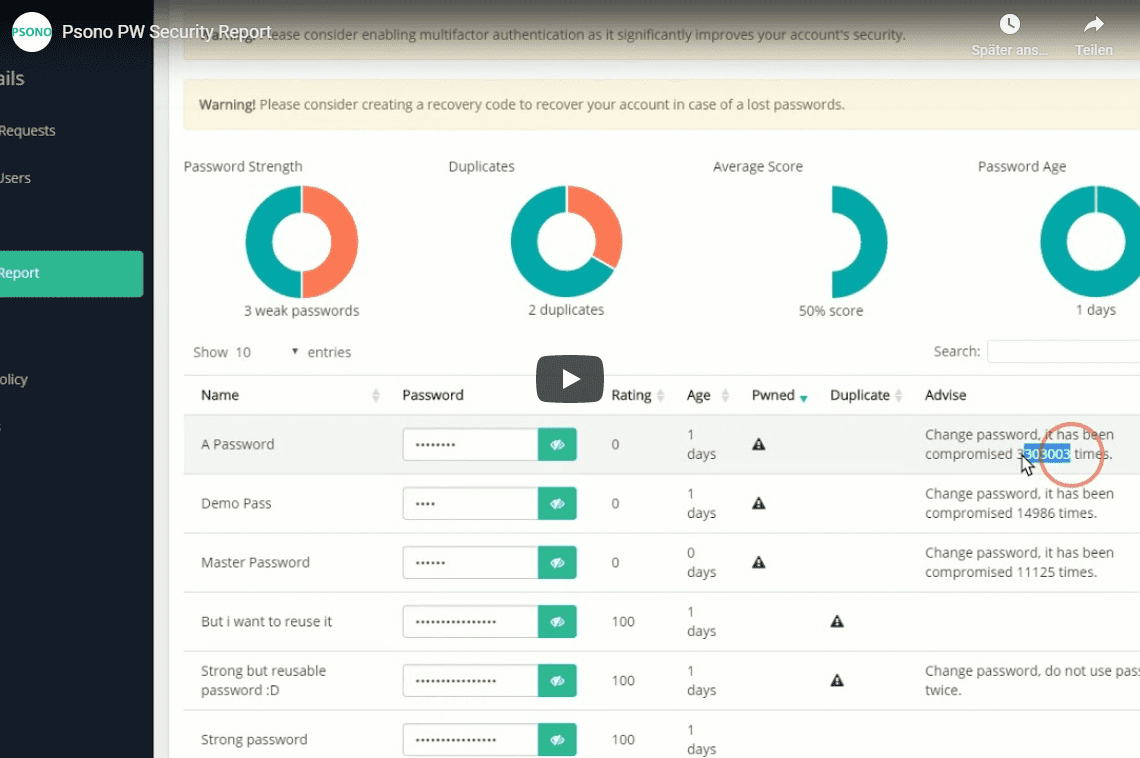
Security report in action!
A small Video giving a better feeling for how it works. The API shows the progress of the analysis. As its a free service we honor the throtteling and dont want to cause any harm, so the requests are limited to one request per 1.5 seconds.
Security Report Features
- Complexity: All entries are checked for their complexity
- Duplicates: Every duplicate that is found gets marked
- Age: People should change passwords regularly
- Breaches: Avoid passwords that have already been compromised
In the background
In a first step all secrets containing your passwords are downloaded from the server. In a second step every secret gets decrypted in your browser before a sha1 hash of the password is created. Sha1 hashes are 160 bits long (40 chars in hex). The sha1 hash is broken into a prefix (5 hex chars) and a suffix (35 hex chars). The prefix is sent to the haveibeenpwned.com API which check its database and return a list of suffixes. The client will compare the suffix of the password against the list of suffixes, that it received and mark the password as breached or not. This is an efficient way to query the password database, without actually sending the password (or weak derivatives) and is known as k-anonymization.